One of the latest buzzwords in the cybersecurity market is SASE, an acronym for secure access services edge. SASE has created a stir in the industry as vendors and providers try to get their arms around what it means and how they can provide SASE-like capabilities to customers.
What is SASE and what are its implications?
Interestingly, as we talk with provider and customer organizations, we are finding there seems to be multiple interpretations. One side of the conversation views SASE as a framework; the other side considers it a solution or product.
SASE is a bundle of network security services that optimize connections to cloud applications. It can be both a framework and a solution. When boiled down, SASE is an amalgamation of existing capabilities that, when combined, creates a new architectural concept that unifies networking and security services.
Core SASE Capabilities
Let’s look at three core capabilities an organization will gain when it pursues SASE transformation.
1. Authentication Gateway Distribution
One of the core principles of SASE is to distribute secure authentication mechanisms closer to the user base, much in the same way a content delivery network (CDN) caches resources closer to those accessing them. This fundamentally changes a traditional hub-and-spoke network topology in which network traffic is funneled through hubs and concentration points (often major office locations or data centers) and then onward to the destination.
Contrary to hub-and-spoke, SASE architecture distributes cloud-based authentication gateways toward a distributed user base. The visual below shows how the topology architecture changes for a distributed network.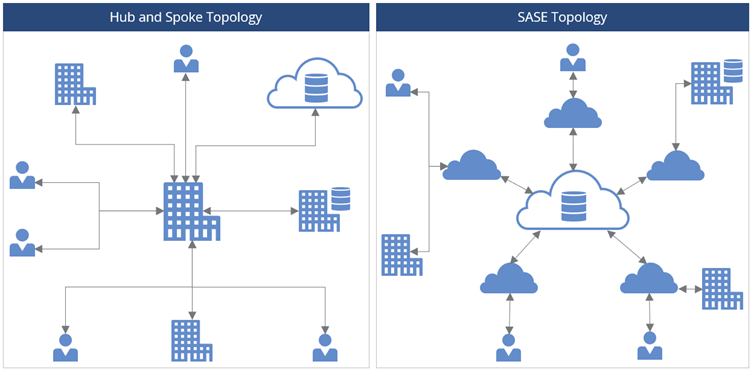
This is arguably the most foundational aspect for SASE transformation because it gives the network the ability to deliver on other complementary capabilities. Because SASE is a cloud-based solution, it allows for a more efficient cost structure by moving services toward the user-base and creates an environment to optimize network traffic and enhance security functionality.
2. SD-WAN Functionality
SD-WAN transformation has been a significant focus for companies in recent years and is also a core capability for SASE. Many organizations have already been working to transform their WAN functionalities so they can more effectively shape traffic and prioritize applications. While SASE incorporates these into its capability set, the difference between SD-WAN and SASE stems from benefits that can be realized by a cloud-based network edge with closer proximity to the user.
Earlier SD-WAN deployments have been heavily dependent on special hardware and software deployed throughout traffic concentration points in an organization’s WAN. While this set up won’t go away completely, movement to a cloud-based SASE architecture redistributes concentration points to catalyze transformation. This factor is emphasized when user bases go remote. Application prioritization can be more targeted and more proactively scalable, and distributed users experience more consistent delivery quality.
3. Zero Trust
Zero trust is another buzzword that gets tossed around the industry, but the core concept is simple: No system should inherently trust any other connecting system. Zero trust is created by mechanisms in the enterprise system that can effectively enforce attribute-based access control. A system can only establish a connection with an access request once the “who, what, where, when, why and how” are verified.
But the reality is that network boundaries are fundamentally shifting – to the cloud and out toward the endpoint where users are connecting to devices. While this may be a boon to workplace productivity, it also means a greater number of entry points into the network and more lateral traffic on the network and via the cloud. A zero-trust enforcement must be incorporated into the environment to ensure an organization’s strong security posture.
As the market solidifies its views on SASE and more organizations take steps to evaluate and implement SASE-driven capabilities, the three factors mentioned above need to be of particular focus. SASE pushes the network’s access boundary toward the users and, by doing so, creates downstream effects for complementary capabilities. Understanding how your network architecture may change with SASE and the subsequent implications can better prepare you to successfully leverage the new capabilities.
SASE is worth evaluation for organizations that are undertaking cloud transformation and innovation. If your organization is considering SASE as a strategic technology initiative, contact us to see how we can help.
