Most organizations today rely on hundreds of third-party suppliers, partners, subcontractors and agents to deliver their services. It’s a matter of doing business. But risks arising out of these relationships are drawing attention from senior management – and rightly so. The high-profile prosecution of enterprises linked to unlawful conduct or compliance failures of their third-party suppliers is a stark reminder of the significance of third-party risk management.
Risk management is about anticipating what negative things might happen to your products or services then mitigating the impact of those negative things. Effective risk management is composed of four basic components: 1) framing the risk, 2) assessing the risk, 3) responding to the risk, 4) and monitoring the risk. An enterprise risk framework addresses systemic issues within an organization and dictates what the risk frameworks throughout the organization should support, based on the strategies across the enterprise. Operational risk management addresses risks related to internal and external operations, including third-party relationships.
Every institution should implement systematic lifecycle management and strong governance practices for their third-party portfolio, especially critical relationships, including with fourth parties.
The ISG Third-party Risk Management (TPRM) Lifecycle Framework pictured here is a model that helps organizations manage the risks in their third-party relationships more effectively.
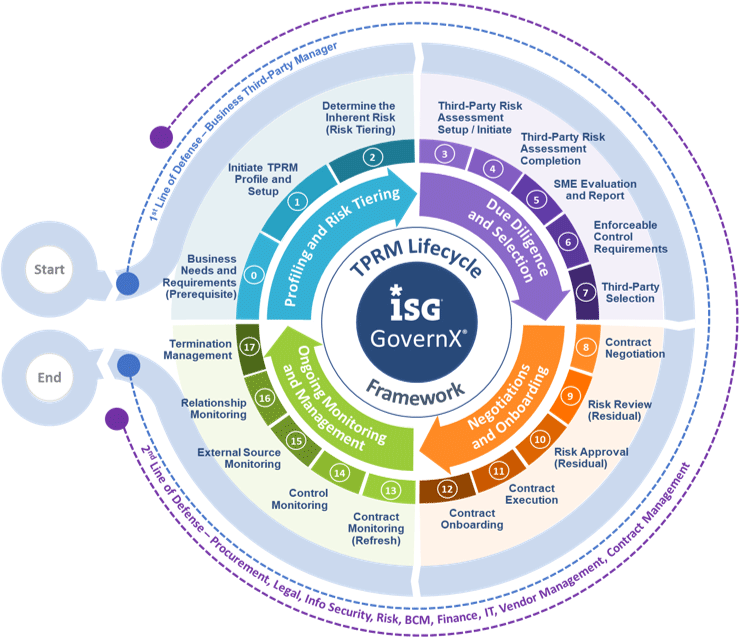
The top half of the ISG TPRM Lifecycle Framework describes lifecycle management activities; the bottom half describes sustainability activities. A robust program includes all the elements in this framework.
1. SETUP AND TIERING
Business and vendor relationship management (VRM) teams are responsible for the following activities:
- Business Plan and Requirements: The starting point of any third-party relationship is the recognition of a need for a better process, solution or service, or when an agreement with the existing vendor is nearing expiry. The next step is to define the business requirements in clear and unambiguous terms.
- Initiate TPRM and Setup: Once the business requirements are defined, the teams should identify and assign the business stakeholders, which are also known as the first line of defense. They play a major role in identifying, assessing, managing and controlling risks related to third-party relationships as they are closest to the operational outcomes, issues and incidents.
- Preliminary Assessments and Risk Tiering: Based on the nature of services from a third-party, an assessment is performed to evaluate the inherent risk. The relationship is then tiered according to its risk.
2. DUE DILIGENCE AND SELECTION
Sourcing, business and VRM teams are responsible for the activities in this phase, which includes evaluation of the third party’s strategic objectives, pending litigation, regulatory violations, industry reputation and risk management practices.
- Third-Party Risk Assessment Setup: Build the inherent risk assessment template, which covers all the elements required to assess risk from third-party relationships.
- Conduct Third-Party Risk Assessment: Route the inherent risk assessment to the first line of defense to determine the risk associated with the third-party relationship.
- Subject Matter Expert Evaluation and Report: Risk control specialists and risk managers will evaluate the responses from the risk assessment and report the scores and risk-tier of the respective third-parties.
- Enforceable Control Requirements: Put appropriate controls in place to manage, mitigate and terminate the risk identified in the risk assessments.
- Third-Party Selection: Choosing the right third-party supplier or partner can mean the difference between having a significant asset or a major liability.
3. NEGOTIATIONS AND ONBOARDING
The contract management, legal, business and VRM teams are responsible for the activities in this phase.
- Contract Negotiation: Contracts that are unambiguous and straightforward without overly legalistic language are vital for effective third-party risk management. Contract clauses should carefully articulate the nature and scope of the engagement, intellectual property rights, right to audit, confidentiality and data privacy.
- Residual Risk Review: Residual risk is the risk that remains after controls are accounted for. It is important to assess the residual risk at the appropriate frequency to ensure the enforced controls are adequate to manage and mitigate the risk.
- Residual Risk Approval: Best practice is to have the business approve or accept the residual risk and determine whether additional controls are required after each residual risk assessment.
- Contract Onboarding: The contract is then onboarded into a technology platform or database, so all the artifacts related to third-party assessments, including inherent and residual risk assessments, responses, respective scores, and controls enforced, are available in one place.
4. ONGOING MONITORING AND MANAGEMENT
The VMO is responsible for ongoing monitoring activities, including contract management, spend management, relationship management and termination management. The VRM and business teams are responsible for risk monitoring and remediation.
- Risk Monitoring and Remediation: Risk monitoring is the most important aspect of third-party risk management. The monitoring should be more detailed and comprehensive if the third-party provides critical services.
- Contract Management: Contract management provides processes, tools and administrative assistance to manage the complex interplay of deliverables, obligations, changes and contract issues.
- Relationship Management: Relationship management facilitates easy administration of governance boards at each layer of customer and third-party relationship management. This also includes setting up an end-to-end performance management framework with service-level agreements and monitors the service delivery against the agreed targets.
- Spend Management: Spend management ensures invoicing is performed according to the contract terms, including conformance with pricing documents.
- Termination Management: The termination phase ensures preparations and a process are in place to efficiently terminate a third-party relationship and transfer the activities either in-house or to another third-party provider.
In the current environment, with so many regulations around data security, privacy and anti-money laundering, organizations have no choice but to extend their risk management practices to their third-party relationships. The goal should be to automate as many of these due diligence and risk assessment processes as possible and minimize tactical work effort. The ISG TPRM Lifecycle Framework and the third-party management platform GovernX® enable organizations to leverage data analytics to develop predictive and proactive risk avoidance capabilities and produce supply chain insights for enhanced business resilience. Contact us to learn more.
